While traditional hacking focuses on infiltrating systems through technical and security flaws, Social Engineering is malicious in its deception. With a focus on exploiting users on a psychological level, hackers find success through manipulating and taking advantage of people’s human behaviours and natural tendencies.
What does a Social Engineering attack look like?
A common technique used to initiate a Social Engineering attack is through sending a potential victim a phishing email. These can look like emails that come from official sources, requesting that you change your password (such as for your email account), or include malicious links that grant hackers access to your information.
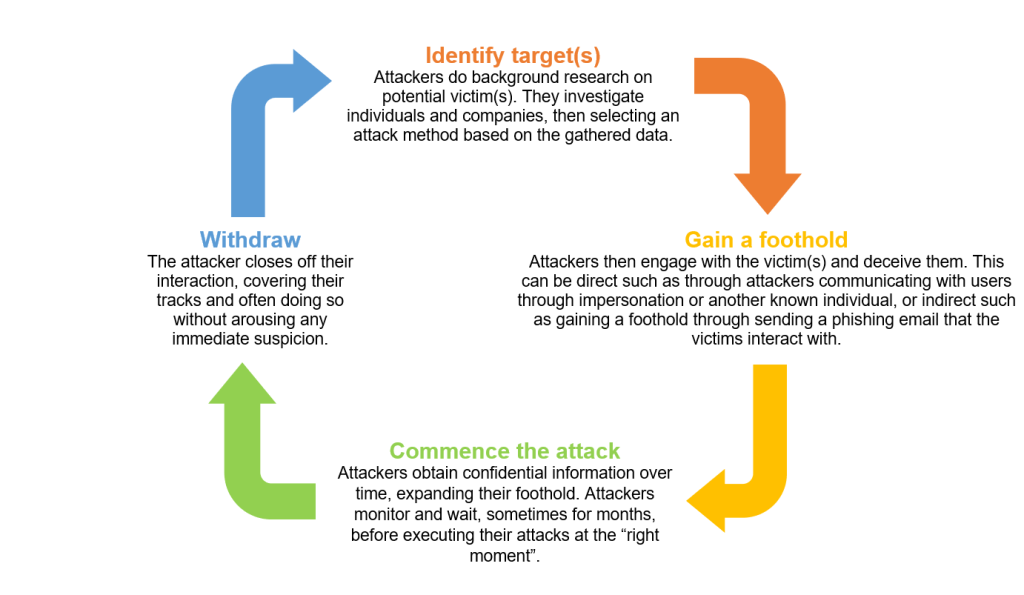
The below table outlines the cycle of a Social Engineering attack:
How do we avoid Social Engineering attacks?
Due to the nature of Social Engineering being an exploit on individuals, traditional protection from malware and viruses will not offer complete protection from a Social Engineering attack. But, there are steps that can be taken to ensure that you stay protected:
1. Never open a dubious email from an unknown source, especially opening attachments or clicking links.
- If you are ever unsure, contact your IT team and they will be able to help you to identify if the email or its content is a risk.
2. Never click on login page links sent in emails, always access the page through your browser.
- It’s especially handy to save bookmarks for all sites you may login to, for quick and secure access.
3. Never share your passwords to your personal accounts, and do not leave sensitive data in open areas (such as a notebook with your passwords on your desk).
- Social Engineering attackers also can infiltrate workplaces physically, if you would like a secure password management solution, Saxons IT can assist in finding something to fit your needs.
4. See something? Say something! Social Engineer attackers don’t just operate virtually.
- An attacker may present themselves in your office as a new hire, a delivery driver, a maintenance person, or anything that they believe will grant them access into the building of the business they want to target. Consider your workplace security, and how accessible it is to those who should not be in the space.
Other Social Engineering attack techniques to be aware of are as below:
Spear Phishing
A more specific and targeted version of “phishing”. This is where attackers often focused on targeting high level individuals from a specific business. Attackers investigate their victims and tailor messages to make the attack as inconspicuous as possible. These attacks are extremely intricate. But, whilst they are difficult for attackers to complete successfully, they often have higher stakes and can be more damaging.
Baiting
These attacks utilise false promises, exploiting a potential victim’s curiosity. Baiting can be online, such as a user receiving an email regarding a topic the attacker has identified the victim may be susceptible to.
Pretexting
Attackers obtain information through cleverly crafted lies and deception. This is often initiated by an attacker impersonating co-workers, financial institutions, or other persons who have right-to-know authority. The attacker then pretends to need sensitive information from a victim in order to perform a critical task, asking security questions you may expect to be asked from the impersonated authority, such as your first pet’s name or the city you were born in. The attacker usually starts by establishing trust with their victim by impersonating co-workers, police, bank and tax officials, or other persons who have right-to-know authority. The “pretexter” asks questions that are ostensibly required to confirm the victim’s identity, through which they gather important personal data.